Faculty for business studies and law, University „Union – Nikola Tesla”, Belgrade
Faculty for business studies and law, University „Union – Nikola Tesla”, Belgrade
1. INTRODUCTION
The prehistoric man was neither aware nor much concerned with the concepts of system and security, but, unambiguously - spontaneously or reasonably and purposefully, he organized around him (created) a „system” that would counter the threats that threaten it. These threats came from other people and the means they used, from living beings (animals), but also from nature itself (rain, city, snow, earthquake). So man was creating a „system of his own security”.
The state, with its basic constituents - territory, population and power - appears at a certain stage of the development of human society. The state becomes the basic subject of international relations, and it remains to this day, regardless of the emergence of other theories and views on the totality of these relations in the age of globalization. Although the security of the individual remains the foundation of the general conception of security, it gains a whole new and much broader meaning and develops into international or national security. The focus of this paper is national-state security. In doing so, the sign of equality between international and national security is conditional.
One of the key levers of force of any state is the army (armed forces). In the conflict, as constants of international relations, the armed forces are emerging as a major security threat. Thus, after the Second World War, there was a continuing danger of the great conflict that was expected between the US and the USSR and the blocs they led (NATO and the Warsaw Pact). With the disintegration of bipolarizations in international relations, the military threat of the widest proportions gained a substitute in the entire corps of the so-called. security challenges, risks and threats, e.g.: terrorism, proliferation of weapons of mass destruction, trafficking in human beings, weapons and narcotics, organized crime and more. These challenges, risks and threats that are human work are always added to natural disasters and disasters that cannot be avoided, although they can be predicted, in part.
2. THEORETICAL DETERMINATION OF CHALLENGES, RISKS AND THREATS
In theory, there are two approaches when it comes to security threats. The first approach, which we find in domestic literature, uses the terms source, form and carrier of threat. In this sense, social, natural and technological-technical sources are distinguished, as are numerous forms and carriers of security threats (Stajić, 2013). The second and more common approach uses the terms challenge, risk and threat. The second approach, which uses the terms challenge, risk and threat, is thought to have arisen under the influence of Anglo-Saxon theory (Mijalković, 2009:91).
2.1. Concepts challenges, risks and threats
When it comes to definitions of challenge, risk and threat, the fact is that they are used in two ways. The first, which views these terms monovalently - as a syntagm (a complex term) and the second that approaches these terms from the point of view of distinguishing them by level of generality and character (Forca, 2019: 46). In theory, there is also an attempt to map sources, forms, and carriers into challenges, risks, and threats. In doing so, the source is equivalent to the challenge, the threat is equivalent to the form, while the risk is the metamorphosis of the challenge into the threat (Mijalković, 2009).
Most analysts distinguish between challenge, risk and threat and define them in a similar way. This implies the following relationships: 1) challenge is a primarily neutral and general term; 2) risk is the notion of less generality than challenge, which initially also has a neutral character but leads more to the threat, and 3) threat is the notion of the lowest level of generality, which has a direct negative relation to a particular security object (Forca, 2016). Sublimating the views of numerous authors, cited in the paper Notional determination of challenges, risks, and threats in the international security system reshaping process (Orlic, 2004: 76-93), Mirjana Milenković in her paper Are Traditional Security Challenges, Risks and threats new forms of security threats globally, regionally and nationally, outlined the following definitions of challenges, risks and threats:
1) The challenge. The challenge is a certain situation that puts security entities to the test with the potential for both positive and negative outcomes. It is a potential form of threat that is initially value neutral, but over time, due to the absence of a reaction, it can gain a negative connotation and grow into risks or threats, as obvious indicators of a security threat. The challenge may be an activity, process, occurrence, some specific event that, by its nature, dynamics and energy, can in certain circumstances influence changes in certain states, beliefs, values, or it can grow into some form of security threat. The possibility of predicting a "challenge" is very small because it is difficult to determine their form of expression, the intensity of the potential threat, the time of expression. Therefore, it can be said that the challenge is generally of a comprehensive and multidirectional character, more general in relation to threat or risk (Milenković, 2016: 750).
2) Risk. Risk is a set of processes and characteristics that contain challenges, that is, potential causes and causes for security threats. The occurrence of risk automatically confirms the possibility of injury or destruction, mainly with a negative meaning. Compared to the challenge, risk is a concept of lower level of generality, in intensity it is more concrete, closer and more likely because it indicates a closer danger, a possible and probable form of threat. The risk is therefore always present only with a greater or lesser degree of likelihood of causing or causing some damage. Unlike the challenge that almost eliminates the possibility of foresight, the risk response can be prepared, the consequences can be managed if they occur, but the risk cannot be eliminated. Unless risk is observed in a timely manner, there are objective opportunities for it to grow into a very concrete threat (Milenković, 2016: 750).
3) Threat. Threats represent concrete actions to injure, destroy, punish, or cause damage to the security subject with short or long-term consequences. The threat has the lowest level of generality, which initially always has a negative sign, because it implies a type of pressure that hints at a specific danger, harm or evil from a position of force, with the aim of forcing a certain security object to make certain concessions or behavior. The threat initially bears strong indications of soon-to-be-damaged issue that will materialize in the absence of a reaction. Threats are most often predictable and potential damages that can cause them are assessable (Milenković, 2016: 750).
2.2. Typology of challenges, risks and threats in theory
In a number of theoretical papers, we encounter an extremely different approach to the typology of security challenges, risks and threats. Therefore, in this paper we will present only characteristic examples from foreign and domestic literature.
1) Pol D. Viliams, discussing the issue - what can be considered a security issue, summarizes the panel discussion at the UN and points out: „One recent illustration of the threat list building policy was Panel 9 - a high-level discussion by the UN Secretary-General on Threats, Challenges and Change (2004), which brought together sixteen prominent international civil servants and former diplomats. After much debate, the Panel Report, A Safer World, distinguishes six groups of threats addressed by world governments: 1) economic and social threats, including poverty, infectious diseases and environmental destruction; 2) inter-state conflicts; 3) intrastate conflicts, including civil war, genocide and other mass atrocities; 4) nuclear, radiological, chemical and biological weapons; 5) terrorism and 6) international organized crime” (Viliams, 2012: 34).
2) World opinion polls are almost indeterminate with security challenges, risks, and threats in the strategies being addressed. Sharon Burke, Senior Advisor to the International Security and Resource Security Program, cites the following dangers in the world public opinion: (1) Islamic militant groups; (2) global climate change; (3) cyber attacks; (4) economic crises; (5) illegal migration of the population; (6) the military power and influence of the US, Russia and China (Burke, 2018).
3) Filip Ejdus provides one general approach to the classification of security challenges, risks and threats (Eidus, 2012: 37-38), which for the sake of clarity is given in Table 1.
Table 1. Classification of security challenges, risks and threats
|
CLASSIFICATION
CRITERIA
|
TYPE OF
CHALLENGES, RISKS AND THREATS
|
|
Security
sector
|
Political, economic,
military, social and environmental
|
|
Origin
|
Internal
and external. Special types are „non-polished” (mixed) or English intermestic
|
|
Source
|
Natural
or human factor
|
|
Carriers
|
Process actors
(state, terrorist groups, criminal groups)
The processes themselves (globalization, for example)
|
|
The
trend
|
Old
and new
|
|
Relation of
forces
|
Symmetrical
and asymmetrical
|
|
Materialization
time
|
The
short, medium and long term
|
|
Degree of
intensity of operation
|
Low,
medium and high
|
Source: Ejdus, 2012:37-38
4) Professor Ljubomir Stajic, in his work (Stajić, 2013) or together with Professor Andrej Savić (Savić, Stajić, 2007), looks at the challenges, risks and threats from the aspect of security threats and determines them as sources, forms and carriers (Table 2).
Table 2. Classification of security threats
|
SOURCES
OF THREATS
|
FORMS
OF THREAT
|
THREATS
CARRIERS
|
|
Social
Natural
Technical- technological
|
1. EXTERNAL
- armed
- unarmed
2. INWARD
- armed
- unarmed
|
Terrorist organizations
Extreme political groupings
Radical
factions within political organizations
Foreign Countries Intelligence
Services
|
Source: Stajić, 2013.
5) Professor Mladen Bajagić, in particular, analyzes only the security challenges and threats, not the risks, and classifies them as follows: (1) world population problems, (2) environmental problems, (3) conflicts, (4) global terrorism, and ( 5) weapons of mass destruction (Bajagić, 2012). While leaving out the term risks, Bajagić believes that contemporary security challenges are: 1) world population problems and 2) environmental problems while contemporary security threats are: 1) conflicts, primarily violent interstate and interstate; global reach terrorism, 2) the spread of conventional and weapons of mass destruction and 3) transnational organized crime (Bajagić, 2012: 48). A broader aspect of Professor Bajagić classification is given in Table 3.
Table 3. Security challenges and threats
|
SOURCES
OF THREATS
|
FORMS
OF THREAT
|
THREATS
CARRIERS
|
|
Social
Natural
Technical- technological
|
1. EXTERNAL
- armed
- unarmed
2. INWARD
- armed
- unarmed
|
Terrorist organizations
Extreme political groupings
Radical
factions within political organizations
Foreign Countries Intelligence
Services
|
Source: Bajagić, 2012: 48.
An insight into the typologies of security challenges, risks, and threats presented in itself indicates the non-unification of theory in this regard. Therefore, it is necessary to apply another approach, i.e. to show how countries, challenges, risks and threats are related.
3. PRACTICAL APPROACH TO SAFETY CHALLENGES, RISKS AND THREATS
A practical approach to security challenges, risks and threats, in essence, is their identification by many countries. The identification of security challenges, risks and threats, in principle, is realized in a document commonly referred to as a national security strategy.
The National Security Strategy, as a document, first appeared in the United States (1987) under President Ronald Reagan (1981-1989 term). Since then, 16 such documents have been brought to the US because every administration in power has an obligation to bring them. The preparation of a document called national security strategy was accepted by the largest number of countries in the world (Forca, 2019: 106).
The national security strategy is not generally the subject of our work, but its content is related to security challenges, risks and threats. The fact is that there is a very different attitude to the content of the document, but challenges, risks and threats are an integral part of it. By analyzing a number of documents, called the National Security Strategy (nine countries) or the Security Strategy (European Union), it can be generally concluded that the contents of those documents are grouped as a whole: security environment analysis; vision and missions; identification of security challenges, risks and threats; identification of national interests and their operationalization to goals; security policy, or mechanisms, instruments and actions to achieve national interests and achieve goals; the implementation of the strategy (principled obligations of the subsystem) and the national security system (Forca, 2019: 109). Just to illustrate, we will list the contents of some national security strategies (Table 4).
Table 4. Content of national security strategies
|
Row.
number
|
SOURCE
|
CONTENTS OF
THE NATIONAL SECURITY STRATEGY
|
|
1.
|
US
National Security Strategy, 2015 (Obama)
|
1. Introduction
2. Security
3. Prosperity
4. Values
5. The international order
6. Conclusion
|
|
2.
|
US National
Security Strategy, 2017 (Trump)
|
President
Trump's editorial
INTRODUCTION
I. PROTECTION
OF THE AMERICAN PEOPLE, THE TERRITORY AND THE AMERICAN LIFE
II. PROMOTION
OF AMERICAN PROSPERITY
III.
ENFORCEMENT OF PEACE BY POWER
IV. STRENGTHENING
THE AMERICAN INFLUENCE
V. REGIONAL
CONTEXT OF THE STRATEGY
CONCLUSION
|
|
3.
|
National
Security Strategy of the Republic of Croatia 2002
|
|
INTRODUCTION
• SAFETY ENVIRONMENT AND CHALLENGES OF
THE REPUBLIC OF CROATIA
• CHALLENGES, RISKS AND FRONT OF THE RH
• SAFETY CONCEPT
• RH SECONCLUSION
CURITY POLICY - AREAS AND INSTRUMENTS
|
|
|
4.
|
National
Security Strategy of the Republic of Croatia 2017
|
|
I INTRODUCTION, VISION AND SAFETY CONCEPT
II NATIONAL INTERESTS
III SAFETY ENVIRONMENT
IV STRATEGIC
OBJECTIVES, INSTRUMENTS AND MECHANISMS FOR THEIR ACHIEVEMENT
V CONCLUSION
|
|
|
|
5.
|
RF National
Security Strategy, 2009.
|
1. General instructions
2. Modern peace, state and trend of development of Russia
3. RF national interests and strategic national priorities
4. National security
5. Organizational, normative, legal and information bases for strategy
implementation
6. Basic presumed national security
|
|
|
6.
|
National
Security Strategy of the Republic of Serbia, 2009
|
Introduction
I
SECURITY ENVIRONMENT
II RISK
CHALLENGES AND FRONT SECURITY
III
NATIONAL INTERESTS IN THE FIELD OF SECURITY
IV.
NATIONAL SECURITY POLICY
IN THE
NATIONAL SECURITY SYSTEM
Conclusion
|
|
|
7.
|
National
Security Strategy of the Republic of Serbia, 2019
|
INTRODUCTION
1. STRATEGIC ENVIRONMENT
2. CHALLENGES, RISKS AND SECURITY SECURITIES
3. NATIONAL INTERESTS
4. NATIONAL SECURITY POLICY
5. NATIONAL SECURITY SYSTEM
6. IMPLEMENTATION OF THE NATIONAL SECURITY STRATEGY
CONCLUSION
|
Source: Forca, 2019: 109.
The European Union, logically, does not have a document called a national security strategy because it is a transnational creation. However, the EU issued two strategic documents in the field of security: 1) EU Security Strategy, 2003 (Isak Fund, Belgrade, 2006) and 2) Global Strategy for the Common Foreign and Security Policy, 2016 (http://www.delmne.ec.europa.eu/code/navigate.php?Id=414, 17.01.2020). The contents of these documents are shown in Table 5.
Table 5. Content of EU security strategies
|
Row.
number
|
YEAR
|
STRATEGY
CONTENTS
|
|
1.
|
2003.
|
Introduction
1. Security environment: current challenges and key security threats
2. Strategic goals
3. Political implications for Europe
Conclusion
|
|
2.
|
2016.
|
Foreword by
High Representative Federica Mogerini
1. A global strategy to promote the interests of our citizens
2. The guiding principles of our external action
3. The priority of our external action
3.1 Security of our Union
3.2 State and social resilience in our East and South
3.3 An integrated approach to conflict and crisis
3.4 Common regional requirements
3.5 Global Governance for the 21st Century
4. From vision to action
|
Source: Forca, 2016: 600.
The number of challenges, risks and threats in the strategies of these countries and the EU is very different (Chart 1).
Chart 1. Number of risk and threat challenges in security strategies
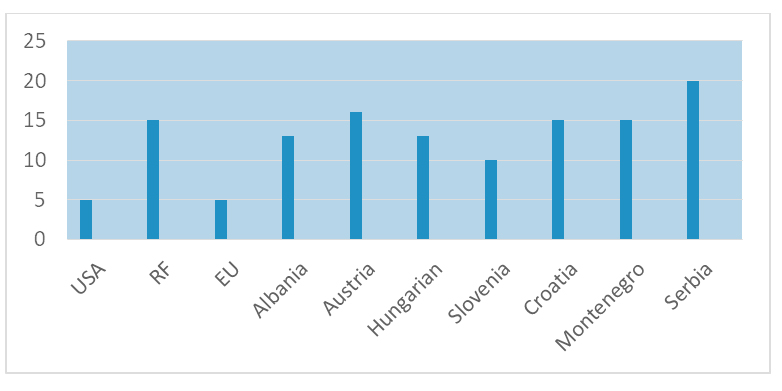
Source: Vitas, 2019: 35.
Graph 1 shows the diversity of the number of identified security challenges, risks and threats in the strategies of the 10 countries mentioned. That number ranges from 4 (USA) to over 20 (Republic of Serbia).
In addition to differences in numbers, the challenges, risks and threats in the strategies of the countries analyzed differ in character (name). Therefore, many authors, when analyzing security challenges, risks and threats in security strategies, usually generalize or determine the frequency of their occurrence. We will show two approaches (Tables 6 and 7).
Table 6. Frequency of security challenges, risks and threats in security strategies
|
Appears in all
strategies
|
Appears in most strategies
|
Appears in a small
number of strategies
|
|
Terrorism
Aggression type attack (international conflict and its
overflow, regardless of the likelihood of that conflict)
The proliferation of weapons of mass destruction
The collapse of states (weakening democracy, corruption
and organized crime)
Economic crisis (significant distortions in economy and
finance)
High-tech crime (information war, cyber threats ...)
Environmental threats (ecological threats, natural and
man-made disasters and disasters)
Health threats
(pandemics, epidemics, etc.)
|
Population migration (large, illegal, etc.)
Lack of natural resources
The misery and poverty of certain regions of the world
The operation of foreign intelligence services
Trafficking in human beings, weapons and narcotics
|
A set of challenges, risks and threats, primarily in
the domestic context, characteristic for each country individually, and so
formulated (for example: unilateral and unlawful proclamation of independence
of Kosovo and Metohija; war in the former SFRY; problems of defining borders
with neighbors ...)
|
Source: Forca, 2016:603.
The previous table shows the frequency of security challenges, risks and threats in security strategies adopted by 2016. After that year, their national security strategies were adopted by the USA (2017), Croatia (2018), Montenegro (2018), Serbia (2019). Thus, according to one study, the dominant challenges, risks and threats in these strategies are presented in Table 7.
Table 7. Dominant security challenges, risks and threats in security strategies
|
Security challenges, risks and
threats
|
USA
|
Russia
|
EU
|
Serbia
|
Montenegro
|
Croatia
|
Albania
|
|
Terrorism
|
+
|
+
|
+
|
+
|
+
|
+
|
+
|
|
Profliferation of weapons of mass destruction
|
+
|
+
|
+
|
+
|
+
|
+
|
+
|
|
Organized crime
|
-
|
+
|
+
|
+
|
+
|
+
|
+
|
|
Migration
|
+
|
+
|
+
|
+
|
+
|
+
|
+
|
|
Information security
|
+
|
+
|
+
|
+
|
+
|
+
|
+
|
|
Energy dependence
|
-
|
-
|
+
|
+
|
+
|
+
|
+
|
|
Economic and social problems
|
-
|
+
|
+
|
+
|
+
|
+
|
+
|
|
Environmental and climate issues
|
+
|
+
|
+
|
+
|
+
|
+
|
+
|
|
Corruption
|
-
|
+
|
-
|
+
|
+
|
+
|
+
|
Source: Rondović, 2018:34.
The following are quantitative indicators of some of the security challenges, risks and threats listed in Table 7.
1) Terrorism. Statistics (Annex of Statistical Information, 2018: 3-4) indicate that during 2017, there were 8,584 terrorist attacks worldwide. 18,753 were killed, 19,461 were injured and 8,937 were killed. The highest number of attacks was in 2016 in Iraq, Afghanistan, India, Pakistan and Indonesia, and by regions Middle East and North Africa 19,121, Sub-Saharan Africa 6,591, South Asia 7,774, Western Europe 238 and Eastern Europe 112. The largest number of attacks were committed. Islamic terrorists (Islamic Republic, Taliban movement, Al-sabab, Boko haram) and Communist Party of India (Chart 2).
Figure 2. Overview of the number of terrorist attacks in the EU
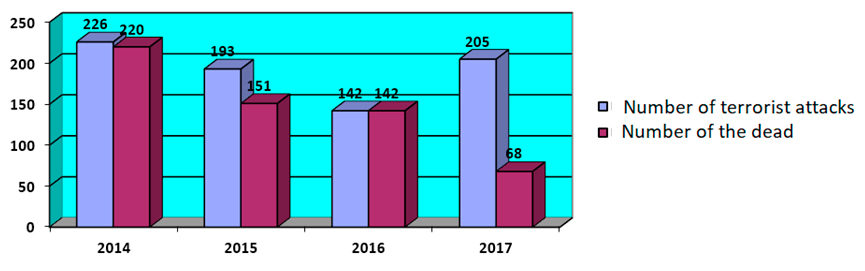
Source: Europol, 2018:9.
2) Organized crime. Organized crime is a threat in all but the US strategies, where it is only cited as a side threat neutralized by good border control. The strategies of the Balkan countries are central to this threat due to large social disparities, unemployment, poverty, economic and transit migration, inequality in education, social protection and other social problems. It is directly related to trafficking in women, children, drugs and weapons (Chart 3).
Chart 3. Crime Index Rate in 2017
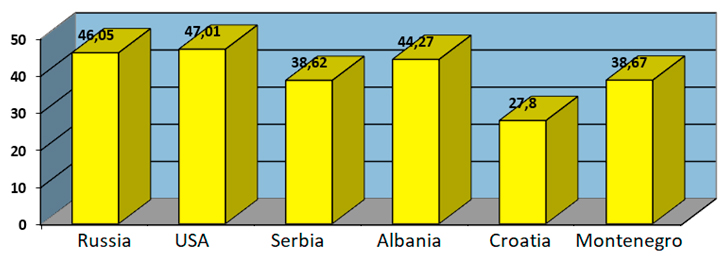
Source: Europe: Crime Index by Country 2018 Mid-Year, https://www.numbeo.com/crime/rankings_by_country.jsp?title=2018-mid®ion=150. (17.01.2020).
3) Illegal migration. The security problems reflected by the occurrence of illegal migration are: (1) the occurrence of possible infectious diseases; (2) the rise of cheap labor; (3) an increase in social and other costs; (4) the occurrence of smuggling and trafficking; (5) negative impact on the economic stability of the country; (6) frequent blockages of borders and roads; (7) conflict between migrants and the police and locals; (8) an increase in criminal activity; (9) the possibility of terrorist acts; (10) Endangering the cultural values of the population. Chart 4 shows the number of illegal migrations in the European Union from 2014 to 2017.
Chart 4. Illegal migration in EU
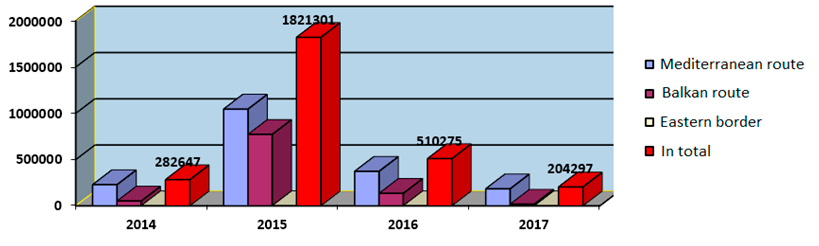
Source: Frontex, 2018:47.
4) Corruption. The United Nations sees corruption as one of its security concerns because it indirectly causes a number of negative factors. Accordingly, the Anti-Corruption Convention was drafted, with the introductory part “The adoption of the United Nations Convention against Corruption will send a clear message that the international community is determined to prevent and control corruption. This will alert the corrupt side that distrust will no longer be tolerated. And this will confirm the importance of key values such as honesty, respect for the rule of law, accountability and transparency in promoting development and making the world a better place for all. ”The following measures will be applied to reduce corruption in the world: (1) Preventive measures; (2) Compliance with the law; (3) International cooperation; (4) Right to property; (5) Technical support and information sharing; and (6) Implementation of prescribed measures (UNSCR, 58/4).
Chart 5. Corruption Perceptions Index in 2017
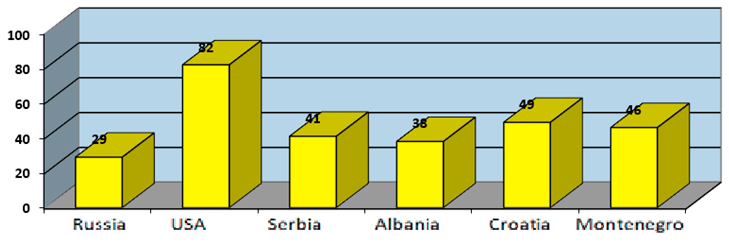
Source: Corruption Perceptions Index 2017,
https://www.transparency.org/news/feature/corruption_perceptions_index_2017 (15.01.2020)
5) Ecological safety. The international community's demand to reduce the effects of climate change and increase of temperature on the planet has resulted in the Paris Agreement. Highly developed countries with a dose of distrust have joined the agreement because of the potential detrimental effects on the national economy. By being elected President of the United States, Donald Trump has fulfilled his election promise and withdrew his country from this agreement even though his country is one of the largest carbon dioxide emitters in the world. This has diminished the image of the US as a country that was thought to be the epitome of green technology and renewable energy.
Chart 6. Countries largest carbon dioxide emitters in 2016
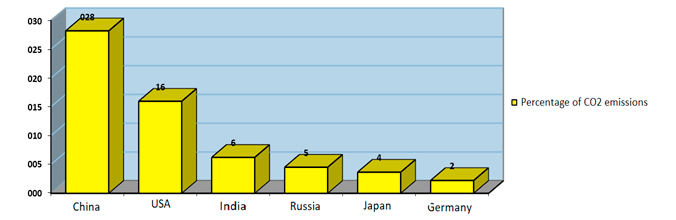
Source: Largest global emitters of carbon dioxide by country 2016,
https://www.statista.com/statistics/271748/the-largest-emitters-of-co2-in-the-world/ (15.01.2020).
3. CONCLUSION
Security is a prerequisite for the survival and development of the world. This theoretically established fact is also recognized in the official documents of international organizations and states as key players in international relations. The essence of understanding national security, among other things, is to identify the challenges, risks and threats to security. Security challenges, risks and threats are under this title in all strategic documents of the analyzed countries. However, the fact is that in theory, the term sources, forms and carriers of security threats also emerge.
The approach to identifying security challenges, risks and concerns is different in theory and practice in the countries of the world. When it comes to national security, it is evident that different countries identify in various ways the security challenges, risks and threats, ranging from four to over twenty in modern strategies. In addition to the difference in numbers, there is also a clear difference in the concretization of security challenges, risks and threats, from state to state. This is understandable, as each state specifies these forms of security threats for its own position. Generalizing the views on security challenges, risks and threats in the nine analyzed countries and the EU, one can conclude that the most frequent are: terrorism; armed conflicts, the possibility of which is reduced but cannot be completely ruled out; proliferation of weapons of mass destruction; collapsed states; economic crises; high-tech crime; endangering the environment and endangering health. Certainly, other security challenges, risks and threats, to varying degrees, as well as country-specific ones are encountered.