Optimizing Perimeter Surveillance Drones to enhance the security system of unmanned aerial vehicles (Case Study: Jordan)
(No. 2, 2021. Security Science Journal)
Mahmod Al-Bkree
Department of Mechatronics Institute of Mechatronics and Vehicle Engineering
Óbuda University, Budapest, Hungary
Research Paper
Received: November 9, 2021
Accepted: December 4, 2021
Abstract: This work is to optimize perimeter surveillance and explore the distribution of ground bases for unmanned aerial vehicles along the Jordanian border and optimize the set of technologies for each aerial vehicle. This model is part of ongoing research on perimeter security systems based on unmanned aerial vehicles. The suggested models give an initial insight about selecting technologies carried by unmanned aerial vehicles based on their priority; it runs for a small scale system that can be expanded, the initial results show the need for at least four ground bases along the length of the border, and a selected set of various technologies for each vehicle.
Keywords: UAV, border surveillance, Optimization, perimeter security

1. Introduction
Perimeter security is a continuous historic challenge, as the facilities rapidly increase in number and sophistication. Advanced modern technologies must be exploited to obtain an adequate level of protection. It secures the outdoor perimeter of any facility, especially if it is with large dimensions. Nowadays, many sites with large areas fall in this range of long perimeter that needs a high level of security (e.g., critical infrastructures, residential compounds, International borders, rivers, etc.). Designing a comprehensive solution based on the Unmanned Aerial Vehicles (UAV) system can aid in solving many problems that come with the current conventional security systems in terms of efficiency, reliability, and cost. The proposed research plan is to study the concept of the UAV systems applied in different environmental conditions to improve the efficiency of the UAV systems. The proposed UAV system is based on modern methods and principles to reach the primary goal of surveillance to provide real-time information and improve the probability of what is known as the 5Ds (Demarcation, Deter, Detect, Delay, and Defeat the intruder). This work is an attempt to apply integer programming optimization techniques to help the overall project design minimize the number of bases and optimize the number of selected surveillance technologies. Transitions from manned vehicles to UAVs for surveillance purposes have been widely adopted by the U.S. military more than other potential operations, as shown in the following figure.
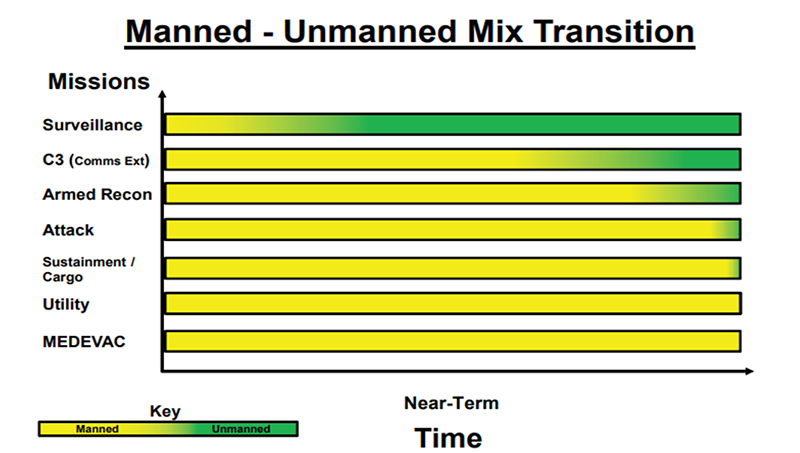
Diagram 1. U.S. Army unmanned aircraft systems roadmap 2010-2035
I used the example of Jordan as a case study for the proposed solution. Jordan is an Arab country of southwest Asia located between N. Latitudes 29° 11' and 33° 22' and E. Longitudes 34° 59' and 39° 12'. Syria borders it to the north, Iraq to the east, Saudi Arabia to the east and south, and Palestine to the west. The country is continuously trying to stop smuggling activities on the border that include drugs and guns and militant foreign personnel. Iraq shares 181 kilometers (112 miles) of international border with Jordan, Syria 375 kilometers (233 miles), Palestine 335 kilometers (148 miles), 26 kilometers (16 miles) of coastline, and Saudi Arabia 728 kilometers (452 miles), adding to 1,645 kilometers (1,006 miles) of total border length.
To cover the whole length, Jordan currently uses physical barriers of walls and fences at some segments of the border, in addition to regular security human resources patrolling areas near the perimeter, as well as multiple layers of technologies including cameras and other types of sensors both permanent fixed and mobile sensors carried on the ground and aerial vehicles. The proposal is to optimize the number of UAVs that are needed for surveillance while at the same time optimizing the number of UAVs operational and maintenance bases together with the quality and quantity of technologies carried by each vehicle. The approach is evaluated from an engineering technological analysis accompanied by an economic constraint. For the system's complexity, we will use a heuristic method whenever a certain estimated or exact information is not available while an excellent practical estimation can be made.
The large variety of sensors and the frequent circumstances changes require multiple optimization needs for the decision-maker; therefore, creating a model to prioritize different options will be helpful; the suggested model can optimize a large set of variabilities. For each scenario, the decision-maker would need to input the distance between the number of potential areas for ground bases and the range on the UAV in kilometers. The model will generate the minimum number of ground bases covering the whole segment.
For model B, the decision-maker will need to input the operational value for each technology and its cost and the budget. The model will select the sensors with the overall maximum value of that given budget.
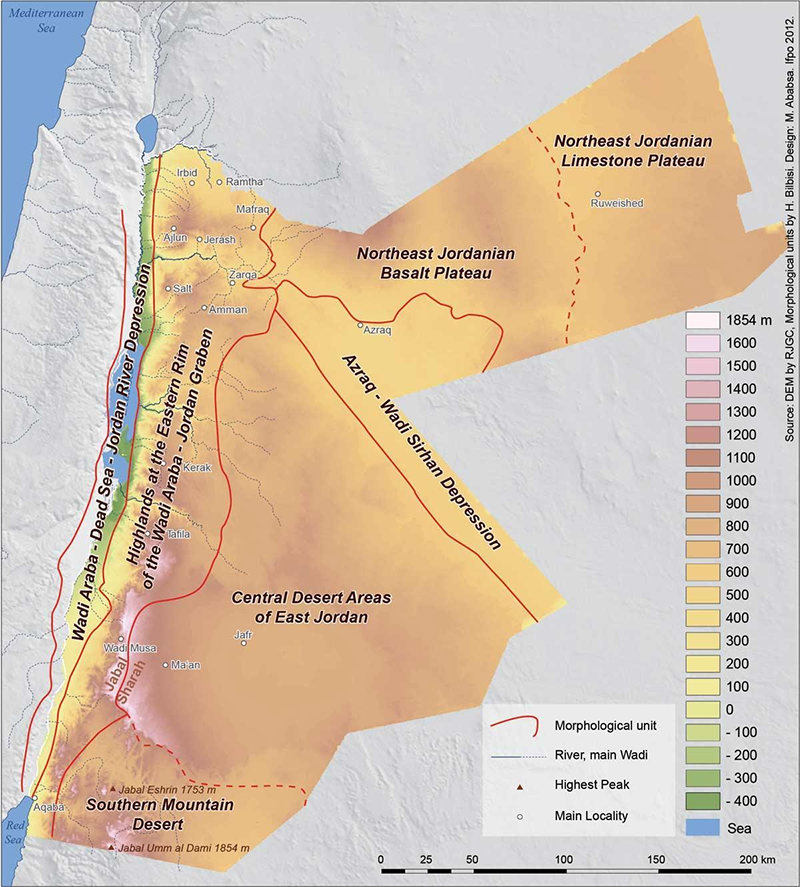
Source: Royal Jordanian Geographic Center – RJGC –
2. Technologies selection
The system is based on adding the element of UAV surveillance to increase the protection level of the border against various threats; each technology will be given a value based on the threat assessments in terms of severity and probability of occurrence, the history of intrusions along a particular segment of the border as well as the natural condition of the different terrains will influence the effectiveness of the countermeasure, therefore, based on the operational value of each technology and its cost the model would prioritize their selection.
The evaluation sequence is as follows:
- Identify which border segment needs surveillance;
- Identify the potential threats for that segments;
- Analyze the appropriate surveillance technology to detect the threats;
- Assign a benefits value for the technology and the cost of acquiring it;
When a segment of the border is to be evaluated considering the terrain of both sides of the borders, in the case of Jordan, the majority of its border is a flat desert plateau and has no natural features that separate both sides, for such segment a camera with night vision would be sufficient and add significant value while for a heavy forest segment a LIDAR technology would add the most value.
The surveillance uses UAV technology as the prime tool and base for the model; UAVs come in many different shapes and forms. Flight range varies from a few meters to several tens of thousands of kilometers. Similarly, and dependably, load weight has a relatively wide range. Lastly, the broad spectrum of technologies and sensors that can be carried and operated on those vehicles, to maximize the field results, a flexible, effective model that can be implemented on a small pilot to be experimented on while at the same time is scalable to orders of magnitudes is aimed for. So the model can start with one UAV carrying one camera and using one ground base for operation and maintenance to multiple of each. Future work is taken into consideration to include a much larger set of technologies based on multiple roadmaps, and our ongoing research results, one of the most under-developed technologies that would be valuable to our model is the "Ground-effect vehicle," which is a good fit for the UAV yet is not utilized. However, the ground-effect is a well-known century-old phenomenon. However, it has not been exploited to its potential, especially on UAV, as the UAV eliminates the main disadvantage of hazardous accidents on human pilots flying near the ground. From my point of view, this single technology would have an order of magnitude improvement on the field of perimeter security using UAV, and such will be added to the model in a later stage.
The following figure shows some selected UAV sensors:
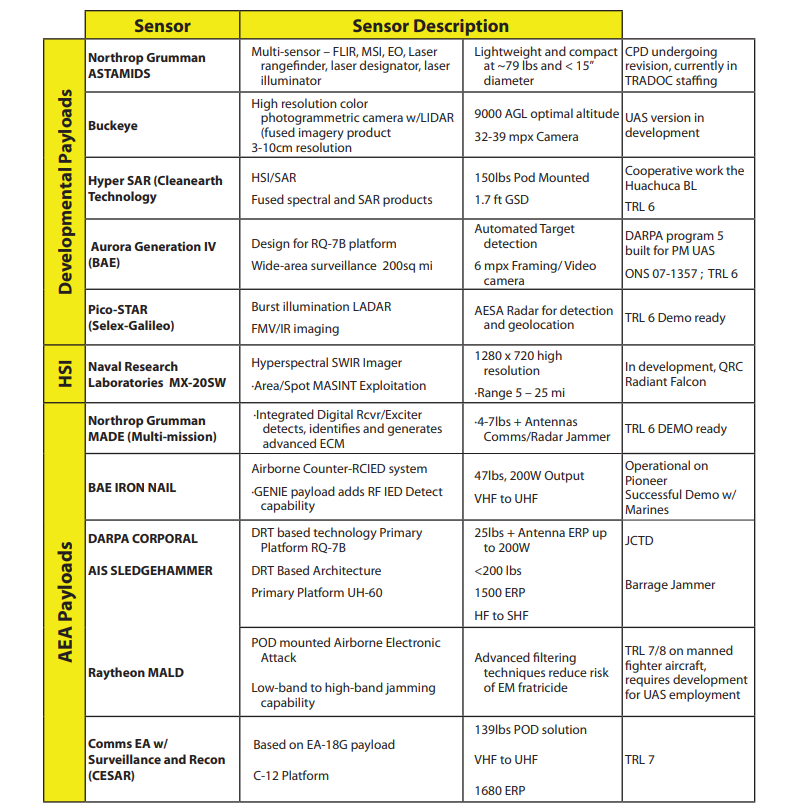
U.S. Army unmanned aircraft systems roadmap 2010-2035
Source: Royal Jordanian Air Force (RJAF) Air Bases
3.1. integer linear programming (ILP) Model Part A
The first, discrete optimization model, the maximum covering formulation based on ten potential base sites in the main cities near the border, finds the minimum number of ground bases that can cover the whole border. Starting from Irbid city as area1 in the northwest and flying counter-clockwise along the border up until Ramtha city as area10, border segments length is 200 kilometers as to have 35 kilometers of overlap between every two segments represented as x1...x10, the UAV flight range is 600 kilometers so the UAV can bypass at least one ground base at a time whenever needed.
The objective function is:
Minimize
Set of constraint:
x10+x1+x2 ≥ 1 (area 1)
x1+x2 ≥ 1 (area 2)
x2 + x3+x4 ≥ 1 (area 3)
x3+x4 ≥ 1 (area 4)
x4+x5+x6 ≥ 1 (area 5)
x5+x6 ≥ 1 (area 6)
x6+ x7 ≥ 1 (area 7)
x6+ x7+x8 ≥ 1 (area 8)
x8+x9 ≥ 1 (area 9)
x9+x10+x1 ≥ 1 (area 10)
(x1,....,x10) are binary.
3.2. Model Part B
A knapsack model is proposed to optimize the number of sensors to be carried on each UAV, as the exact vehicle can cover the whole border, it will have at least two bases to land for maintenance and refueling, no one technology can be selected (n+1) independent times unless all other needed technologies got selected for at least (n) times, the following table shows the technologies costs and operational values for the Camera, Lidar, Physical/Biological samples collectors (PBSC), Hyperspectral Camera, Radar, Telecommunication human to machine means (TCHM), Object installer capability (OIC).
|
|
Camera
|
Lidar
|
PBSC
|
Spectral
Camera
|
Radar
|
TCHM
|
OIC
|
|
cost (thousands)
|
1
|
20
|
28
|
15
|
1
|
5
|
40
|
|
value
|
100
|
60
|
55
|
90
|
90
|
70
|
100
|
Given a budget of $80,000, the following model is used to maximize the values/cost. Yj represents technology (1 if selected, 0 otherwise).
The objective function is:
maximize 100x1 + 60x2 + 55x3 + 90x4 + 90x5 + 70x6 + 100x7
Set of constraint:
x1 + 20x2 + 28x3 + 15x4 + 1x5 + 5x6 + 40x7 <= 80
4.Results
Applying the above models Shows that at least four ground bases are needed to cover the length of the border (x2,x4,x6, and x9). Technology-wise running the model result of selecting (4 Cameras, three radars, 2 TCHM, 1 Spectral Camera, and 1 Lidar). However, from a practical view, the result, in this case, shows a repetitive selection of the same technology reducing the overall operational value. In contrast, other technologies were not selected due to budget limitations. An additional 2000 dollars to the budget would get six different technologies (all except PBSC).
5. Conclusions
A linear programming optimization is a valuable tool for complex system design; it can provide an insight into a large set of variability; in this work, the initial model works well as a proof of concept; the next step is scaling up and including more considerations, such as future expectations of the challenges, and what kind of new technologies would be introduced, adding models and increasing the dependencies among them will be critical for the solution, and require high difficulty level of model formulation. More Mixed Integer Programming (MILP) techniques will be investigated to have a central and holistic approach to the problem at hand. The proposed system was selected by factoring in the security needs for the targeted user (Jordan in this case) to have a chance of implementation, a small yet scalable pilot experiment that utilizes the current infrastructure of the Jordanian border security.
References
- [1]. Szabolcsi, Róbert. "3D FLIGHT PATH PLANNING FOR MULTIROTOR UAV." Review of the Air Force Academy 1 (2020): 5-16.
- [2]. Al-Bkree, Mahmod. "Slat armor to protect critical infrastructure." Haditechnika 54, no. 3 (2020): 17-19.
- [3]. Szabolcsi, Róbert. "A new emergency landing concept for unmanned aerial vehicles." Review of the Air Force Academy 2 (2016): 5.
- [4]. Szabolcsi, Róbert. "The Developing Military Robotics." In Proceedings of the 13th International Conference of "Scientific Research and Education in the Air Force," "AFASES, vol. 2011. 2011.
- [5]. Al-Bkree, Mahmod. "Man-Tracking and Sign Cutting by Surveillance UAV." In 2019 IEEE SmartWorld, Ubiquitous Intelligence & Computing, Advanced & Trusted Computing, Scalable Computing & Communications, Cloud & Big Data Computing, Internet of People, and Smart City Innovation (SmartWorld/SCALCOM/UIC/ATC/CBDCom/IOP/SCI), pp. 253-256. IEEE, 2019.
- [6]. U.S. Army unmanned aircraft systems roadmap 2010-2035.
- [7]. Bitay, Enikő. "2018-A XXIII. Fiatal Műszakiak Tudományos Ülésszak programja ." (2018).
- [8]. A. Basudhar and S. Missouri, "Adaptive explicit decision functions for probabilistic design and optimization using support vector machines," Computer & Structure, vol. 86, no. 19–20, pp. 1904–1917, 2008.
- [9]. https://www.nationsencyclopedia.com/geography/Indonesia-to-Mongolia/Jordan.html#ixzz6wFOMDbzp
- [10]. Lajos, Berek, Szabolcsi Róbert, Vass Attila, and Temesvári Zsolt. "Hetyei Csaba; Kiss Sándor; Szlivka Ferenc."
- [11]. Bathla, Yatish, and Mahmod Al-Bkree. "Web application for 3D software comparison considering PLM system." Hadmernok 13, no. 1 (2018): 302-313.
- [12]. Rardin, Ronald L., and Ronald L. Rardin. Optimization in operations research. Vol. 166. Upper Saddle River, NJ: Prentice-Hall, 1998.
- [13]. Salter, Mark B., and Can E. Mutlu. "Psychoanalytic theory and border security." European Journal of Social Theory 15, no. 2 (2012): 179-195.
- [14]. Derrick, Douglas C., Aaron C. Elkins, Judee K. Burgoon, Jay F. Nunamaker, and Daniel Dajun Zeng. "Border security credibility assessments via heterogeneous sensor fusion." IEEE Intelligent Systems 25, no. 3 (2010): 41-49.
- [15]. Doerner, Karl F., Walter J. Gutjahr, Richard F. Hartl, Christine Strauss, and Christian Stummer. "Pareto ant colony optimization with ILP preprocessing in multiobjective project portfolio selection." European Journal of Operational Research 171, no. 3 (2006): 830-841.
- [16]. Abdou, G., and J. Arghavani. "Interactive ILP procedures for stacking optimization for the 3D palletization problem." International Journal of Production Research 35, no. 5 (1997): 1287-1304.