Strategic Approaches to Digital Transformation in Tanzania: A Geopolitical Perspective
(Vol. 5 No. 3, 2024. Security Science Journal)
George S. Oreku, The Open University of Tanzania, Dar Es Salaam, Tanzania
Research Paper
Received: November 11
Accepted: December 18
Abstract: Tanzania has achieved impressive political, economic, and social progress in recent years. However, the country continues to face considerable development challenges, such as economic inequality, population growth, and corruption. At the same time, new opportunities, such as digital transformation, have the potential to drive necessary changes and reforms. This paper explores digital transformation in Tanzania, considering its geopolitical realities and the immense opportunities it creates. A combined survey data approach was used to gather comprehensive information. The findings reveal that digital transformation, in conjunction with Tanzania’s geopolitical realities, can generate significant opportunities for the country. Tanzania’s strategic location is a significant advantage for fostering digital transformation. The study recommends that the country capitalize on ongoing digital transformation initiatives and geopolitical factors to overcome economic stagnation.
Keywords: geopolitical, digital transformation, security, cyber, data.

1. Introduction
Global dependence on digital systems makes countries highly vulnerable to data flow disruptions. Maintaining global data flows is crucial for social stability, economic prosperity, and national growth. Disruptions to e-commerce, e-banking, and platform services like Airbnb and Uber could cause significant economic disruption.
Digital transformation is the process of using digital technologies to create new or modify existing business processes, culture, and customer experiences to meet changing business and market requirements while geopolitics is a method of studying foreign policy to understand, explain, and predict international political behavior through geographical variables. We argue that developments in Digital transformation, and the related impact on international business, can be better achieved by revisiting Geopolitical stability which requires a country that hold structural power to exercise this power with due consideration for those that do not.
Global geopolitics heavily depends on access to major internet cables carrying internet traffic between countries and continents. Currently, over 90% of global internet traffic flows through submarine cables, often following the same geographical routes used by telegraph cables in the 19th century ( Douglas et al, 2017). For Tanzania, the country utilises cables termed as the National ICT Backbone, that was designed to cover all regions and districts, spanning approximately 10,000 km Dhliwayo J, ( 2005) .
The analysis of Digital Transformation opportunities together with the geographic features of the Country and space are all important to monitor with the purpose of identifying threats, vulnerabilities, and related risks to the same. The purpose is to ensure that information that is created, processed, stored, retrieved and disseminated through Digital Transformation and humans, remains confidential, has its integrity untouched, and is available to those that have the right to access that information. It is evident that as technology has had huge positive transformational impacts on societies, the same can be misused by threat actors, ranging from states, state sponsored threat actors, to organised crime groups and lone-wolf actors. Thus, as 5G-technologies are implemented, 6G-technology-seminars are held, to ensure that societies still thrive from these technologies, it is important that current and future leaders, professionals and technologists, work to ensure a safe, secure, and trustworthy Internet.
Taking into account that Cybersecurity is one of the clearest examples of the interconnection between technology and geopolitics, this has been recently proven by large-scale hacks appeared to target US Government intellectual property and intelligence. But the effects were far wider because the attackers hacked widely used software, exposing tens of thousands of companies and government agencies, and revealing back doors other hackers can infiltrate. Geopolitically driven cyberattacks can have significant implications for cybersecurity, risk management and digital transformation strategy. While no company is immune to cyberattacks, companies with strong cyber defenses and data protection systems, and those with employees that exercise good cyber hygiene, are likely to be less at risk.
The Tanzanian tech entrepreneurship ecosystem analyzed in this paper with the sense to improve digital transformation and foster a thriving start-up environment was inline with some finding in Tanzania. The College of Business Education's research on data mastery in Tanzania found that over 70% of respondents cited inadequate consumer protection as a deterrent to e-commerce transactions, suggesting that existing legislation has not adequately addressed issues of distrust and online fraud concerns,Ulimboka, L., et al (2020).
The article focuses on cybersecurity initiatives and service gaps, with key findings from interviews with local institutions indicating the importance of legal aspects. On analysis of the technology entrepreneurship ecosystem, the study identified service gaps such as the safety of conducting business online outlining the gaps with regards to cybersecurity and the law. This echoes a survey by ,Mwasomola, et al (2020) which suggested that existing legislation has not adequately addressed issue of distrust and online fraud concerns.
The Tanzania Cybercrime Act 2015, enacted in April 2015, criminalizes computer system and information technology crimes in mainland Tanzania. It governs the investigation, collection, and use of electronic evidence, with Article 50 exempting Zanzibar. The Act aims to protect Tanzanians from cybercrime but has identified key issues related to device access and possession, including illegal access, interception, data intrusion, espionage, system intrusion, forgery, and fraud. Other crimes covered include aiding and abetting, attempted crimes, conspiracy, and offenses related to critical infrastructure. The law outlines measures to ensure protection from cyberattacks and fair data use.
Tanzania lacks strong consumer rights advocacy bodies despite existing legislation like the Cybercrime Act 2015, Electronic and Postal Communications Regulations of 2018, TCRA (2018), and Bank of Tanzania (2019). Part VI of the Electronic Transactions Act includes provisions for online consumer protection, but these have proven inadequate in addressing online security concerns. Enforcing existing provisions is a major challenge, and comprehensive revisions are needed to clarify mechanisms for seeking legal remedies and handling complaints and disputes. Tanzania recently enacted a new Cyber Security and Personal Data Protection Act (2023)capitalizes on digital transformation.
The new Act in Tanzania strengthens enterprise security protocols, aiming to mitigate risks from insider threats and external cyberattacks, which impact business profiles and operating models. This will protect brands, company assets, and build trust. Cybersecurity is crucial for digital transformation, as business goals rely on IT solutions and technology. The Act introduces restrictions on the collection and processing of personal data, and a data protection law was presented to Parliament on September 7, 2022. Tanzania drew inspiration from existing data protection laws to develop its own legislation, Personal Data Protection (2023).
Tanzanian businesses and universities are embracing cloud-based solutions for digital transformation, but this requires robust data security. The benefits are evident, but this transformation requires comprehensive and robust data security, María M. et al (2023). The risk of breaches increases as more data is transferred to the cloud, with malicious actors exploiting weaknesses. Executive of e- Infrastructure at JISC, Steve Kennett,(Steve K.S., (2023)) emphasizes the need for awareness and simple steps to protect data.The author cites example during the COVID-19 pandemic, emphasizing the importance of data protection when the increased risk associated with rapid shift to remote working and cloud adoptions was being highly practiced.
The world economy is evolving due to digital technology. Digital transformation (DT) has been prioritized by organizations seeking to maintain a competitive advantage in the era of the Fourth Industrial Revolution. DT is integrated into everyday life, including higher education Schwab, K.( 2016). However, many nations have not fully realized the positive developmental effects of digital technology, including inclusive and sustainable growth, improved governance, and responsive service delivery. Tanzania is undergoing DT driven by the increasing number of people connected to communication and internet services. This DT is impacting the country’s economic and socio-cultural frameworks through enhanced key services and improved productivity in economic sectors, Okeleke, K. (2016). as evidenced by the measuring survey on the Tanzanian Information Society and Digital Ecosystem.
In light of the significant shift in competitive advantage brought about by digital technology, Tanzania needs to acquire seven “digital pivots”. These pivots represent a broad range of assets and capabilities required to develop truly digital government services presented in figure 2 below. According to a survey of government officials from Tanzania, these digital pivots positively impact their organizations.Protecting digital information from unauthorized access, corruption, or theft throughout its lifecycle is essential for achieving the intended goals of any digital transformation initiative. This protection can be ensured through technical measures or legal frameworks.
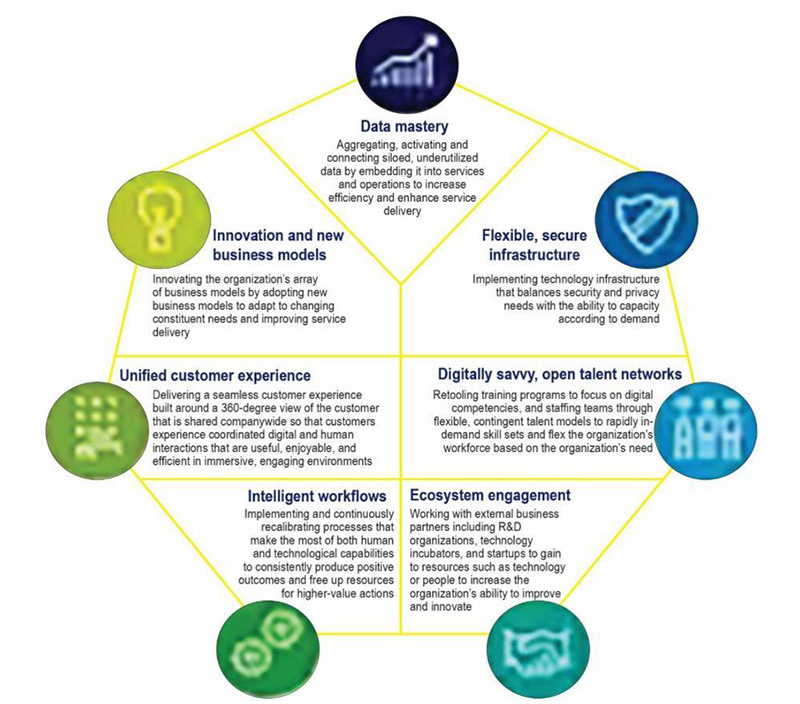
Figure 2. The Seven Digital Pivots to Propel an Organization’s Progress Toward Digital Maturity
Source: Author
2. Research Design
This research utilized both qualitative and quantitative methodologies to collect and analyze data from respondents using a survey tool incorporated into a mobile app. The survey tool was designed to cover four target groups: the general public, district municipalities/councils, corporate companies, and teachers/students. The research process involved a collaborative approach, with stakeholders engaged in requirements solicitation, mobile app design and development, data collection, and analysis.
For the digital transformation and technological ecosystem analysis, a survey of over 3,000 respondents from six wards in the Kinondoni Municipal was conducted. The survey was randomly distributed to respondents from diverse backgrounds, including public groups, companies, teachers, and students.
The need to combine data from multiple surveys can arise for various reasons. Combining data from two or more independent surveys can lead to larger sample sizes, providing more information and greater precision (Lohr and Raghunathan, 2017). To obtain a larger population sample and insights into attitudes that are difficult to measure using observational approaches, data from all collected survey was combined.
The responses were analyzed to understand the digital maturity of the organizations sampled. Respondents rated the positive business impact of each of the seven digital pivots within their organization. Responses for each pivot were aggregated, with higher scores indicating greater maturity. Organizations were then categorized into high, medium, or low maturity based on a normal distribution.
This research was conducted in Tanzania, a nation with rich historical, political, and social heritage, making it an excellent case study for geopolitical analysis. Tanzania shares ethnic backgrounds, social connections, geographic similarities, cultural ties, colonial history, and trade relations with several East African countries. As a member of the East African Community (EAC), Tanzania holds a significant position compared to other member states: Kenya, Uganda, Rwanda, Burundi, and South Sudan, allowing the study's findings to be broadly applicable. Although the research did not include the other five EAC member states due to data collection challenges, this omission did not compromise the reliability or validity of the results.
The research employed a randomly sampling approach, aligning with the interpretive model that prioritizes understanding participants' perspectives to gain insights into issues relevant to the study's aims, Patton, M. Q. (2002). Randomly sampling approach focused on selecting cases that provide rich information for analysis. Given Tanzania’s large population of approximately 65 million, including everyone in the research was impractical. Therefore, a sample size calculation method was followed,Gomm, R. (2008). Gomm [idem]. For populations exceeding 1,000,000, a sample size of 384 was considered adequate.
The study identified individuals and organizations directly involved in the digital transformation process, including government officials from various ministries, particularly those involved in foreign affairs and East African Community matters, representatives from international organizations, academic institutions, and the cross-border business community at key entry points with partner states. The research randomly included members of the cross-border business community operating at principal entry points between the EAC and Tanzania.
Data collection methods included questionnaires, interviews, observations, and the analysis of government documents, videos, recordings, newspapers, letters, and books. Data was sourced from two primary avenues: primary data collected directly from participants in Tanzania, including key individuals from government ministries and academic institutions, and secondary data from various Tanzanian institutions, such as the University Library, as well as books, newspapers, government documents, journals, articles, and archival resources.
3.1 Characteristics of the respondents
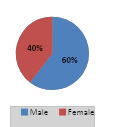
Table 2: Demographic Background - Age Group
|
18 – 30
|
1445
|
47
|
|
30 – 45
|
1174
|
38
|
|
45 – 55
|
356
|
12
|
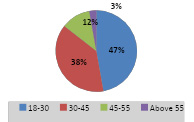
Table 3: Demographic Background - Education Level
|
Primary
|
731
|
23
|
|
Secondary
|
1433
|
44
|
|
College
|
632
|
20
|
|
University
|
402
|
12
|
Table 4: Mobile Ownership and Internet Subscription
Note: Respondents from district municipalities/councils did not complete this section.
Table 5 No. of ICT Projects and Broadband Connections
Table 6: No. of Internet Service Providers
Table 7: ICT Infrastructure, Teachings, and Literacy in Schools
|
Teach ICT
|
66
|
19
|
|
Have ICT Teachers
|
73
|
21
|
|
Use ICT as Educational Tool
|
91
|
26
|
|
Have Computer Lab
|
66
|
19
|
Table 8: Most Used ICT Applications by Teachers at Schools
3. General Technological Embracement in Tanzania
From the extraction of the literature review its envisaged that the future of the modern workforce relies on technology. Technology is poised to transform work processes and offer greater flexibility for increased output. However, reluctance to embrace new technology can hinder a country's progress.
Digital transformation in Tanzania involves integrating digital technologies into every aspect of institutional operations, economic condition, enhancing productivity, efficiency, and customer engagement using technologies such as cloud computing, big data analytics, artificial intelligence (AI), and the Internet of Things (IoT).
The implementation of the National ICT Broadband Infrastructure (NICTBB) was part of the Tanzania National ICT Policy (NICTP) developed in 2003 and later recognized by the Government of Tanzania in the National Development Vision 2025 for its importance in accelerating the achievement of goals and objectives outlined in the National Development Vision 2025 and the National Economic Growth and Poverty Reduction Strategy (Pazi el al, 2013).
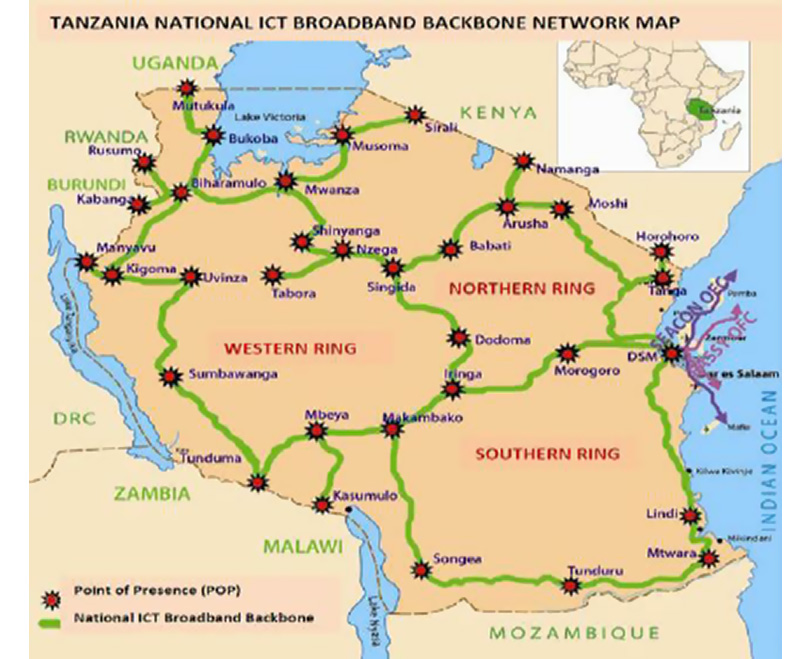
Figure 1: Tanzania National ICT Backbone Network diagram, Zaipuna (2011)
Internet cables are a tangible aspect of data geopolitics. Damage to cables can disconnect an entire country from the internet, with profound economic and political consequences. The 2008 severing of major internet cables near Alexandria, Egypt, demonstrated these consequences for users and businesses in the Gulf region and India Ziady H. (2024) .
Terrestrial cables are increasingly supplementing submarine cables, providing greater diversity in data traffic routes. The Digital Silk Road (DSR), part of China’s One Belt – One Road initiative, aims to connect Eurasia with fiber-optic cables laid along newly constructed railroads and energy pipelines.
Detailed information on internet traffic hubs and digital geopolitics is available in works by Kurbalija Kurbalija, (2024) and in “The impact of (big) data on geopolitics, negotiations, and the diplomatic modus operandi”. This study highlights ongoing initiatives and the need for capacity building and awareness-raising within Tanzania and its organizations regarding digital transformation and data usage. It stresses the importance of improving data management in Tanzania to facilitate user-friendly access. Kurbalija (2024) emphasises the importance of data and digital transformation on the activities of the diplomatic services and the different economies through digitally enabled business models and digitally based service delivery.
Tanzania's history with digital policies has been mixed. Confusing terminology led to the rejection of the Freedom of Information Draft Bill in 2006, and the Data Protection Bill faced criticism in 2014 for being ineffective. However, lessons learned from these experiences have informed the development of the Tanzania Cybercrimes Act and the Personal Data Protection Act (2015), which have been successful. These efforts are expected to facilitate digital transformation.
A case study research project, “Digital Identity in Tanzania,” examined socio-digital ID systems in 10 African countries. This study highlighted the importance of expanding digital adoption and establishing a secure and reliable digital economy, Boshe, P. (2021). Trust is a key component of this process. Cybersecurity and data protection regulations can foster trust in online transactions and protect internet openness. Tanzania’s approach to digital governance seems to lean towards regulatory radicalism, with recorded instances of digital rights violations. While national security is paramount, there is evidence suggesting that mass surveillance tactics may be driven by political motives. Despite existing laws on cybersecurity and electronic communications, improvements are still needed.
Digital transformation (DT) is an ongoing process fundamentally changing the economy and society, Meske, C, & Junglas I. (2020), Kitsios, et al, (2023). DT often anifests through the rapid and continuous adoption of new information and communication technology (ICT) solutions. With the support of ongoing initiatives in Tanzania, this can be readily achieved if viewed as an opportunity.
The government, with support from international actors and development partners, has launched extensive interventions to address the digital divide. The landscape of development cooperation on digital issues is complex. Tanzania has relied on foreign loans and grants from partners like the World Bank, South Korea, European Union members, and China to fund its digital initiatives. These partners exert influence over the types of initiatives they support. Tanzania must maintain ownership and ensure that externally funded projects align with national interests. Tanzania has three primary options for technological advancement:
• Develop indigenous technology through innovation, discovery, and creativity. This relies on the availability of a skilled workforce, funding, supportive policies, and effective institutional arrangements.
• Share technologies with other countries.
• Combine technology sharing with indigenous development.
Research has identified critical innovation support steps that can be replicated in developing nations, including Tanzania, providing an overview of investment potential for start-ups. Analysis indicates that the start-up ecosystem in Dar es Salaam is nascent but developing.
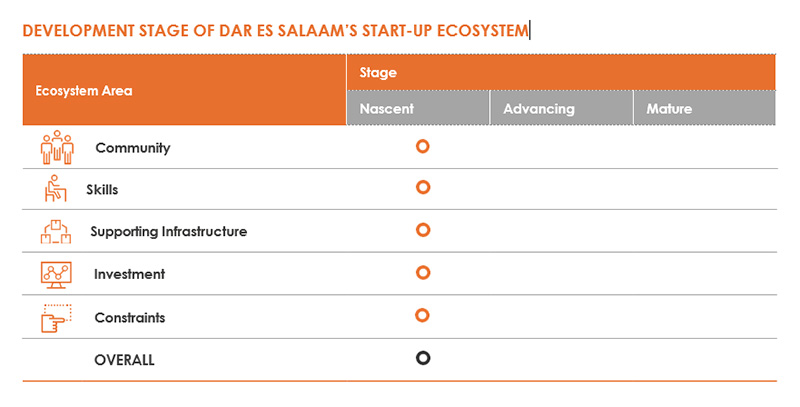
The evidence from our analysis points to the conclusion that the start-up ecosystem in Dar es Salaam is at a nascent stage that is just beginning to develop (see Table 4-6).
Tanzania faces a technology deficit due to its ineffective approach to both indigenous technology development and knowledge and technology transfer. Innovation inputs are weak, jeopardizing innovation activities. Although developing nations benefit from accessing and sharing globally available technologies, Tanzania only occasionally utilizes technology transfer strategies. Figure number 2 demonstrates the potential of start-ups in contributing to Tanzania’s digital transformation initiatives with the necessary legal support.
This study findings propose four phases for engaging with start-ups to achieve digital transformation objectives: engage, empower, expand, and sustain.
Engage: Utilize digital content intelligence and engagement to strengthen, extend, or modify the customer value proposition, then focus on integrating digital processes.
Empower: Begin by developing and integrating digital operations. Then address the customer value proposition to complete the transformation.
Expand: Create new capabilities aligned with the redesigned customer value proposition and operational strategy.
Sustain: Maintain ecosystemic, performance, and competitive advantage.
Organizations and the private sector are capitalizing on technological advancements by utilizing their unique qualities and capabilities as catalysts for positive change. This supports the digital transformation process, encourages new ways of thinking and working, and reshapes businesses. Organizations need cutting-edge facilities to enhance connectivity and conversion, analyze large datasets, provide employees with tools to empower the digitalization process, and accelerate anticipated growth. Many organizations and the government are recognizing the need to seize this opportunity.
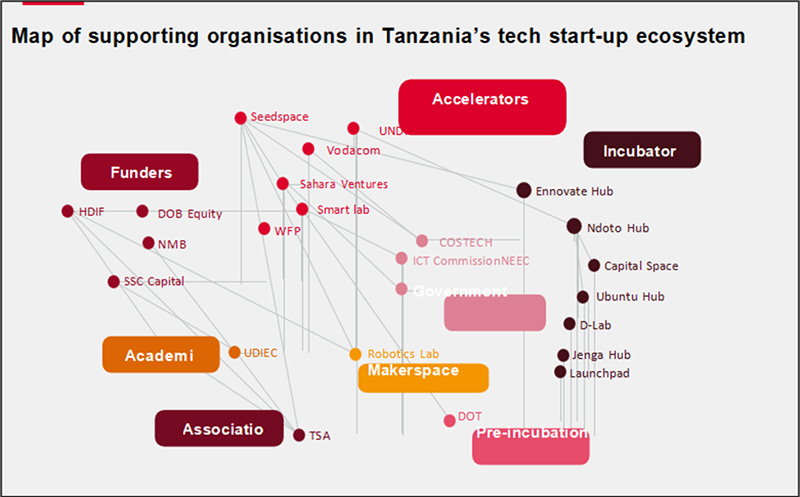
Figure 2: Map of Supporting Organizations in Tanzania’s Tech Start-up Ecosystem
Source: International Trade Centre
Figure 2 depicts the organizations supporting start-up growth in relation to digital transformation assistance. The following issues need to be addressed to ensure start-up success:
- A demand for programs tailored to enhance digital literacy among entrepreneurs in the informal sector.
- Limited and fragmented innovation support hub initiatives. Improved collaboration is needed for increased sustainability.
- Inadequate support systems for start-ups during the early-stage or pre-revenue phase, as entrepreneurs struggle to implement viable business models.
- Tech start-ups need digital upskilling in product development, investor preparedness, and marketing.
While technology-only initiatives are largely interconnected, there are few technology-focused institutions. This can be partly attributed to other institutions viewing technical support as a universal need for all entrepreneurs, negating the need for further specialization.
Viewing technology as a cross-cutting issue is particularly relevant when supporting technological applications in traditional sectors such as e-commerce, marketplaces, classifieds, adtech, agtech, autotech, cleantech, edtech, fintech, healthtech, real estate tech, regtech, space tech, marketing tech (loyalty apps), transportation, and travel and tourism tech. However, the ecosystem should also prioritize supporting start-ups developing solutions for emerging sectors, including AI, big data/data and analytics, virtual/augmented reality, gaming, the Internet of Things, smart homes, cybersecurity, blockchain, robotics, and drones.
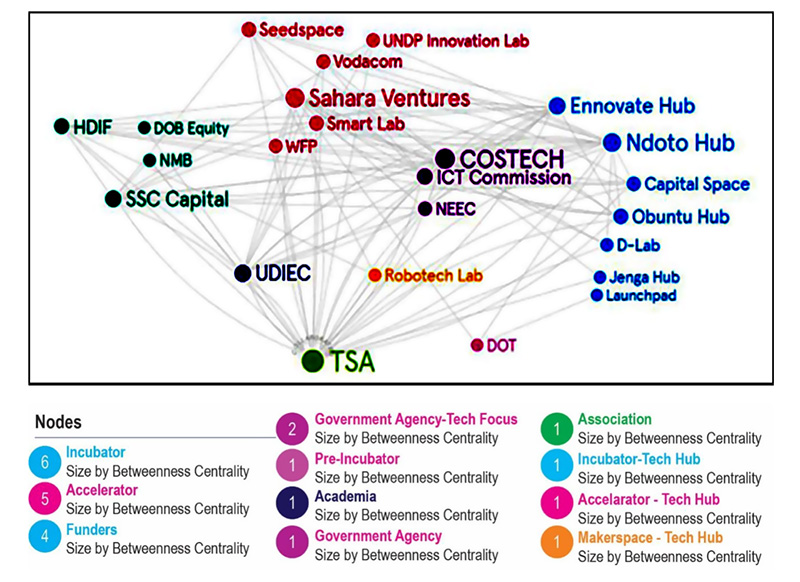
Figure 3: Tanzania’s Tech-Focused Ecosystem
This presents an opportunity for existing institutions to support these new hubs and focus on providing services to fill existing gaps in the ecosystem which is an avenue the country can venture on.
4. Geopolitical Realities
Throughout the study and particularity this section what stands out is the depth qualitative data which were analyzed, distilled, and organized into relevant themes.A randomly sampling approach identified prevalent themes, their contexts, and interrelationships, Patton, M. Q. (2002). Data from surveys, interviews, and focus groups were cross-checked to ensure the reliability of the findings. However quantitative data were also examined using descriptive analysis methods, including statistics describing, compiling, and visually representing key constructs of interest. Inferential statistics derived from these findings were assessed to draw conclusions about relationships between variables. Charts, graphs, and tables were used to illustrate and compare scenarios or other information best presented quantitatively.
To understand Tanzania's geopolitical landscape, the study examined all attributes affecting the country, dissecting each element to understand the current status quo. The research focused on economic conditions, personal safety, theft experiences, and evaluations of business strategies and technological implementations in Tanzania.
To understand the geopolitical situation in Tanzania the study used analysis of survey responses using selected questions to extract anonymous feedback from randomly respondances guided by ten questions:
Qn 1:
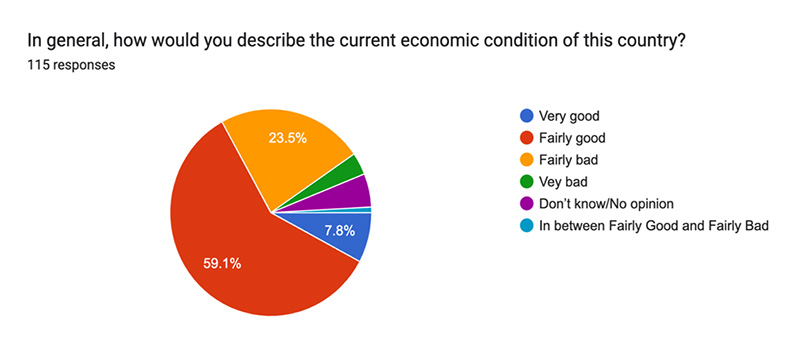
Survey results indicated that most Tanzanians are satisfied with their country’s economic conditions, with 59.1% rating it as “fairly good” and 7.8% as “very good” out of 115 responses. Many interviewees believe that Tanzania is moving in the right direction, despite concerns about the country's overall trajectory.
Qn 2:
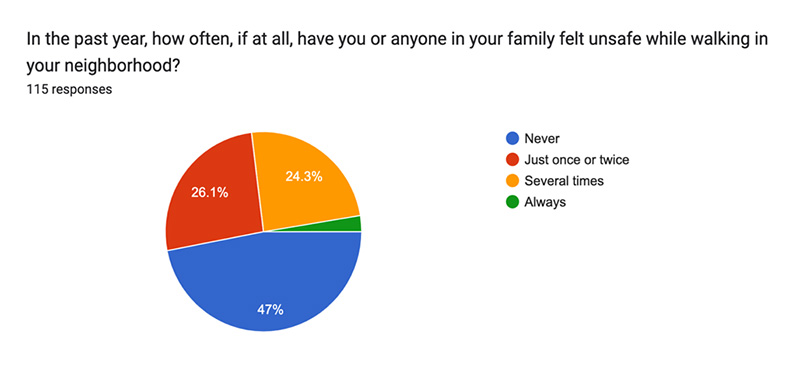
Most Tanzanians generally feel safe and have not experienced theft or violent attacks, but significant minorities have not been so fortunate. Of 115 respondents, 47% reported “never” feeling unsafe walking in their neighborhood.
Qn 3:
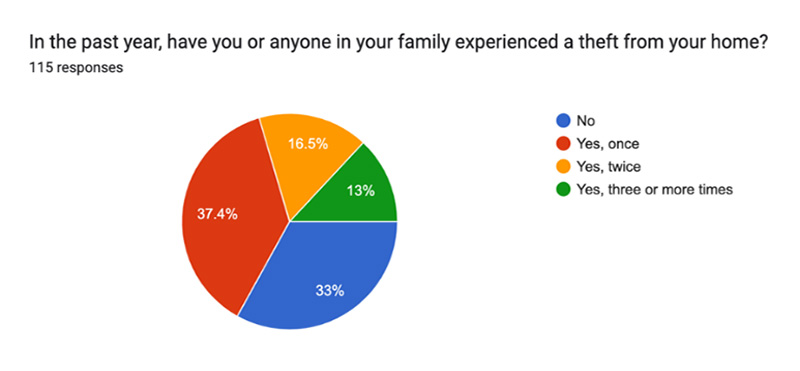
37.4% of respondents reported experiencing theft at home once in the previous year, 13% reported multiple thefts, and 33% reported no thefts.
Qn 4:
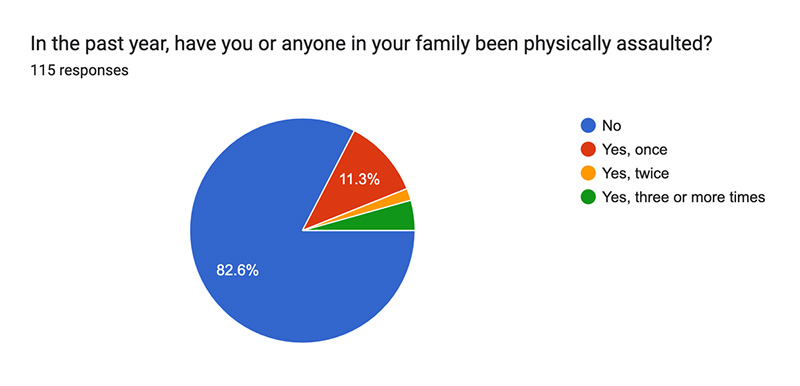
Of 115 respondents, 82.6% reported never experiencing physical insults against close relatives, while 11.3% reported one such incident. A small proportion expressed at least “a little bit” of fear of political intimidation or violence during election periods based on observations from neighboring countries. The study found that only 21.7% feared becoming victims of political intimidation or violence.
Qn 5:
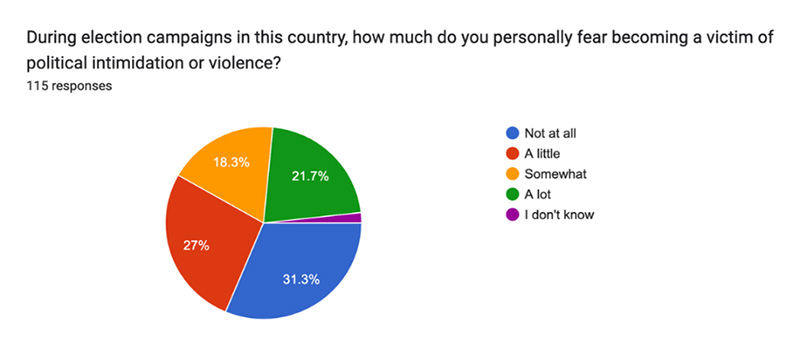
Reasons for not reporting crime to the police vary across countries. In Tanzania, the primary reason cited was the lack of police presence or the distance to the police station. Other reasons included fear of reprisal from the attacker and reporting the crime to other authorities like local government or traditional leaders. Out of 115 respondents, 34.8% did not report incidents to the police, while 35.7% did.
Qn 6 & Qn 7:
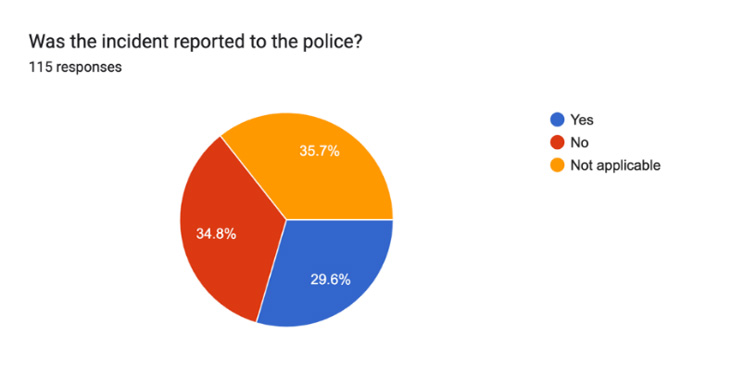

If victims of crime, a majority of Tanzanians would first seek assistance from someone other than the police. The main reason (48% of respondents) was the expectation of being asked for money or bribes in exchange for assistance, while 19% believed the police would not listen or show concern. Consequently, 40.9% would prefer to seek help from family or friends.
Qn 9:
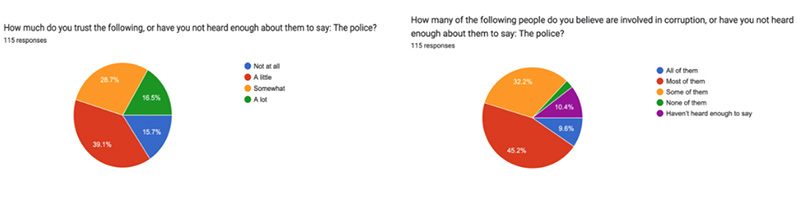
The army is trusted more in Tanzania than the police. Overall, [Redacted]% of Tanzanians trust the army “somewhat” or “a lot.” Consistent with low levels of trust in the police, 39.1% of Tanzanians perceive “most” or “all” police officers as corrupt. Public perception of police corruption has fluctuated over time, but is currently lower in Tanzania than in 2002/2003.
Qn 10:
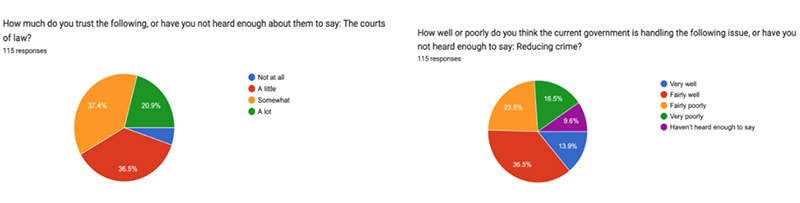
Courts of law are trusted less than the army but more than the police, with two-thirds (36.5%) of Tanzanians expressing “somewhat” or “a lot” of trust in the courts, compared to other East Africans.
Over half (36.5%) of those surveyed on government performance in addressing crime believe their government is doing “fairly well” or “very well” in combating crime. Tanzanians' ratings of government handling of crime improved between 1999 and 2006, but have declined since 2008.
Tanzania’s crime and security landscape, while relatively competitive regionally, is deficient globally. Financial crimes, particularly money laundering, are prevalent, and economically motivated petty crimes and sexual violence are increasing. The police force's capacity to combat crime is limited, further hampered by allegations of bribery and corruption. Terrorist organizations operating in neighboring regions, particularly Mozambique, pose a significant cross-border attack risk. Concerns about democratic regression and the potential for internal conflict are rising as Tanzania approaches its 2025 general elections.
The report by BMI (2024), a Fitch Solutions company, examines the crime and security risks faced by foreign business travelers, expatriates, and organizations operating in Tanzania, using the BMI’s Crime and Security Risk Index, which covers 170 states worldwide. The report provides research and data on defense spending and trade in Tanzania, potential catalysts for military conflict, and terrorism and political violence risks. It evaluates the military’s ability to counter threats, considering the international strategic context and Tanzania's counter-terrorism capabilities.
The study also investigates organized crime within the region and assesses police force capacity and integrity. It analyzes corporate governance culture, highlighting potential reputational risks for businesses from corruption and money laundering. The report outlines the necessary due diligence for higher-risk jurisdictions and includes historical data from the defense sector, an analysis of the armed forces, insights into the domestic defense market, and defense spending projections for the next five to ten years.
The study identifies poverty as a significant contributor to rising crime rates, as individuals turn to illegal means to acquire financial resources. The National Bureau of Statistics (NBS) released a 2023 report outlining crime and road safety statistics, supporting this finding. The report, based on data from the Tanzania Police Force, reveals that 607,102 criminal incidents were reported in 2023, compared to 574,881 in 2022, representing an increase of 32,221 crimes, Byemelwa, A. (2023).
The report further details that 53,640 incidents were classified as major offenses, while 553,462 were categorized as minor offenses. This represents a slight decrease from 2022, which recorded 54,123 major and 520,758 minor incidents. Among minor offenses, theft-related crimes were most prevalent, totaling 258,488 cases, followed by crimes against individuals at 171,858, and moral offenses at 123,116.
Theft-related offenses increased by 7.6% in 2023, from 21,767 to 23,414 incidents. This category includes various criminal activities such as armed robbery, highway robbery, armed theft, violent robbery, burglary, general theft, motorcycle and vehicle theft, livestock theft, arson, and financial crimes. Burglary constituted 51.57% of all reported incidents in this category, followed by motorcycle theft with 3,861 cases, livestock theft with 3,762 cases, and violent robbery with 1,327 cases.
Offenses against individuals, including murder, rape, sodomy, child abduction, child neglect, and human trafficking, rose to 13,748 incidents in 2023, up from 11,118 in the preceding year. Rape was the most frequently reported crime, with cases increasing from 6,827 in 2022 to 8,691 in 2023. Sodomy also saw a significant rise of 56.9%, increasing from 1,586 cases in 2022 to 2,488 cases in 2023.
Homicides decreased from 2,464 incidents in 2022 to 2,303 in 2023. Moral offenses also experienced an overall reduction, with 15 out of 16 specified crimes showing a decrease. Bomb possession was the only exception, rising from one incident in 2022 to three in 2023. Total moral offenses decreased by 22.4%, from 21,238 cases in 2022 to 16,478 in 2023.
The highest number of minor offenses occurred in the police regions of Kinondoni (57,404), Mwanza (47,220), Ilala (36,806), Temeke (34,500), and Morogoro (30,474). Conversely, the regions or units reporting the lowest number of minor offenses were Tazara (70), Marine (97), Ports (109), Airports (129), and Railways (186).
A research initiative was conducted using a randomized survey to gain insights into the security and geopolitical context in Tanzania. The aim was to understand public perceptions, identify key challenges, and discern emerging trends related to national security, political stability, and external influences affecting the region. The findings provide a nuanced analysis of factors shaping Tanzania's security environment and geopolitical position. The methodology employed involved online questionnaires combined with a mobile application for data collection and management and a web dashboard for data collector oversight, analysis, and visualization.The activity was conducted after technical discussions between the Open University of Tanzania (OUT) technical team and selected government officials before sharing the response link.
The research utilizes a descriptive-analytic methodology based on logical reasoning. The study uses primary data, documentary research, and library resources to explore the subjects and issues addressed in the findings. The aim was to identify fundamental factors influencing both independent and dependent variables, making an exploratory design appropriate for this objective. Qualitative research emphasizes understanding, elucidating, uncovering, and clarifying the circumstances, emotions, perceptions, attitudes, values, beliefs, and experiences of specific groups of individuals.
5. Conclusion
This study recommends that Tanzania adopt a more pragmatic and assertive approach in its foreign economic relations. Rather than limiting itself to exclusive trade agreements and technology partnerships, Tanzania should leverage its current geopolitical landscape and the opportunities presented by digital transformation. It's crucial for Tanzania to enhance regulatory measures and security protocols to mitigate data and cybersecurity risks associated with 5G technologies.
Data integration into centralized systems is fundamental to digital transformation, but it also increases vulnerability to cyber threats. A comprehensive strategy is needed to address these risks. In digital transformation, strategy should be prioritized over technology. While changes to IT architecture may be necessary, enhancing strategic thinking is more important.
Several factors drive the growing acceptance of digital transformation, including increased availability and use of digital technology, supportive legal (Tanzania Data Act 2023, Drafted ICT Policy 2023) and infrastructure evolving consumer and worker expectations, and the need for organizations to remain competitive in an increasingly digital environment.
Traditional diplomacy poses significant challenges for small states due to financial constraints. Digital diplomacy can be a valuable tool for these nations, enabling them to conduct diplomatic activities more effectively. Digital diplomacy is not just used for foreign policy goals but also as part of the digital economy, which has become central in the coronavirus era. This highlights the link between diplomacy and economics. African agencies like Brand South Africa, Kenya, Ghana, and Botswana can be a good example for Tanzania and adopt digital diplomacy and place-marketing initiatives to effectively manage her reputation and promote her Digital Transformation.These insights are valuable for formulating strategies related to security, economic policy, business management, and technology deployment in Tanzania.
References
- Applegate, L.M. Austin,R.D. McFarlan,F.W. (2006), Corporate Information Strategy and Management, McGraw-Hill/Irwin Custom Publishing
- Bank of Tanzania (2019), The Bank of Tanzania Regulations
- Boshe, P. (2021), African Data Privacy Laws, 161-187, 2016. 3, 2016. Data Protection Legal Reforms in Africa. Research ICT Africa, 2021.
- Byemelwa A (2023)“Poverty Sparks Crime Surge in Tanzania: New Statistics Unveil Alarming Trends” https://panafricanvisions.com/2024/07/poverty-sparks-crime-surge-intanzania-new-statistics-unveil-alarmin trends/#:~:text=The%20report%2C%20which%20gathered%20data,an%20increase%20of%2032%2C221%20crimes. Accessed on July 23, 2024
- BMI, a Fitch Solutions Company (2024), “Tanzania Crime, Defence & Security Report,Accessed on 1st October 2024, https://store.fitchsolutions.com/crime-defence-security/tanzania-crime-defence-security-report)
- Corbin, J and Strauss, A. (1990), Grounded Theory Research: Procedures, Canons, and Evaluative Criteria, Qualitative Sociology (Human Sciences Press, Inc). Vol. 13, No. 1.
- CYBERCRIMES ACT". tanzanialaws.com. Archived from the original on 2017-09-12. Retrieved 2023-05-15.
- Douglas R.B & Carter L.,(2017), International Submarine Cables and Biodiversity of Areas Beyond National Jurisdiction: The Cloud Beneath the Sea, 2017, pp. 1-72 (72 pages)
- Dhliwayo, J., (2005) Developing a Fiber Optic backbone for Africa.
- Disney A., (2020), Social Network Analysis - Cambridge Intelligence https://cambridge-intelligence.com/social-network-analysis/
- Fuze, CIO Outlook (2017), Driving Digital Transformation
- Gomm, R. (2008). Social Research Methodology, A Critical Introduction, 2nd Edition, New York: Palgrave Macmillan.
- Gomm [idem]
- Huskaj G,(2023), Digital Geopolitics: A Review of the Current State. Geneva Centre for Security Policy, Geneva, Switzerland
- Kurbalija J, (2024) “The impact of big data on geopolitics, negotiations, and diplomacy” Updated on 10 April 2024, Accessed on 8th October 2024,https://www.diplomacy.edu/blog/impact-big-data-geopolitics-negotiations-and-diplomatic-modus-operandi/
- Kitsios, F., Kamariotou, M. and Mavromatis, A. (2023), “Drivers and Outcomes of Digital Transformation: The Case of Public Sector Services”, Information, Vol. 14 No. 1, p. 43, doi: 10.3390/info14010043.
- Kumar, R. (2014). Research Methodology, 4th Edition, London: Sage Publications.
- María M. F C et al (2023), Is digital transformation threatened? A systematic literature review of the factors influencing firms’ digital transformation and internationalization, Journal of Business Research Volume 157, March 2023, 113546.
- Mwasomola, et al (2020), Examining the Consumer Protection and Comprehensiveness in E-Commerce in Tanzania, Business Education Journal, Volume IV, Issue I
- McCaffrey et al, (2024), How to factor geopolitics into technology strategy, Access on13 November 24 https://www.ey.com/en_gl/insights/geostrategy/how-to-factor-geopolitical-risk-into-technology-strategy.)
- Meske, C, and Junglas I. (2020). Investigating the elicitation of employees’ support towards digital workplace transformation. BEHAV. Inform. Technol. 39, 1-17.doi:10.1080/0144929X.2020.1742382
- Oreku G., (2021) A Rule-based Approach for Resolving Cybercrime in Financial Institutions: The Tanzania case, February 2021,Huria Journal of the Open University of Tanzania 27(1 DOI:10.61538/huria.v27i1.870
- Okeleke, K. (2016). Digital Transformation in Tanzania: The Role of Mobile Technology and Impact on Development Goals. GSMA Intelligence Orr, D.,
- Patton, M. Q. (2002). Qualitative Research and Evaluation Methods, 3rd ed. (Sage Publications Inc).
- Pazi S, et al (2013) “Last mile connectivity issues facing National ICT backbone” Conference: The International Conference on E-Technologies and Business on the Web EBW2013) May 2013. DOI:10.13140/2.1.4706.0163, Bangkok, Thailand.
- Personal Data Protection (2023), c. 12. Available at: https:// chrome-extension://kdpelmjpfafjppnhbloffcjpeomlnpah/https://www.mawasiliano.go.tz/uploads/documents/sw-1691159153-GN%20NO.%20449C%20OF%202023.pdf (Accessed: 4 April 2023
- Steve K. S., (2023),” Why data security is so important in the age of digital transformation”, https://www.timeshighereducation.com/hub/amazon-web-services-digital-innovation-higher-education, Accessed on 12.05.2023]
- Schwab, K. (14 January 2016). The Fourth Industrial Revolution: What it means, how to respond, Retrieved from https://www.weforum.org/agenda/2016/01/the-fourth-industrialrevolution-what-it-means-and-how-to-respond/
- Sawy O.A. El & Pereira. F., (2013) Business Modelling in the Dynamic Digital Space: An Ecosystem Approach, Springer, Heidelberg
- TCRA (2018), The Electronic and Postal Communications (Consumer Protection) Regulations 2018.
- Tanzania Cybercrimes Act (2015) and the Personal Data Protection Act
- Tanzania: Cybercrimes Bill Enacted | Global Legal Monitor". www.loc.gov. Goitom, Hanibal. 2015-06-15. Retrieved 2023-05-15.https://www.computer.org/digital-library/magazines/it/ai-for-digital-transformation
- Ulimboka, L., et al (2020), Examining the Consumer Protection and Comprehensiveness in e-Commerce in Tanzania Business Educational Journal
- Weller, M., & Farrow, R. (2019). How is Digitalization Affecting the Flexibility and Openness of Higher Education Provision? Results of a Global Survey Using a New Conceptual Model. Journal of Interactive Media in Education, 1(3). https://doi.org/10.5334/jime.523.
- Zaipuna Y., (2011) National ICT Broadband Infrastructure Backbone Project.
- Ziady H, CNN (2024) “Red Sea cables have been damaged, disrupting internet traffic” Accessed on 9th October 24, https://edition.cnn.com/2024/03/04/business/red-sea-cables-cut-internet/index.html